Hot.com appears to be a search platform designed to help users find services or businesses related to adult entertainment across various locations worldwide. It emphasizes anonymity and no tracking for its users, offering a way to search without leaving a digital footprint.
However, my research showed that anonymity might not be the case here. I engage twice with the website.
Executive Summary
The case study details a scam encountered on Hot.com, a platform for adult entertainment services. Following interaction on the site without VPN protection, the victim faced threats and demands for money, highlighting risks such as privacy breaches and social engineering scams. This incident serves as a crucial reminder of the importance of cybersecurity measures like VPNs to maintain anonymity online and protect against potential cyber threats.
The Adversary’s Actions, Tactics, and Delivery Methods
The first time, I chose a random provider and texted, “Hi there.” The second time, I did not engage with anyone at all. Also, I did not use my VPN when I visited this website. The next day, “Tony Gonzales” contacted me, claiming that I stole $3000 from one of his escorts. Naturally, he is looking to collect that money. It was not just a text message from Tony that contained my home address, a picture from my social media, and more information. I also received a phone call from him. Tony was rude and mentioned that he knew my entire blood life and that they would all suffer if I didn’t pay. How is he going to “make us pay”? Well, the cartel will have to get involved in either collection or in the process of hurting us.
I must say that Tony was rather persistent. He called multiple times and changed the story. First, it was his escort, then it was the cartel’s escort, and lastly, it was something along the lines of “me screwing around on their (cartel’s) website, and for that, I have to pay.” When I asked him, “Do people pay?” he replied, “Yes, motherf$%^er, and you will too!”

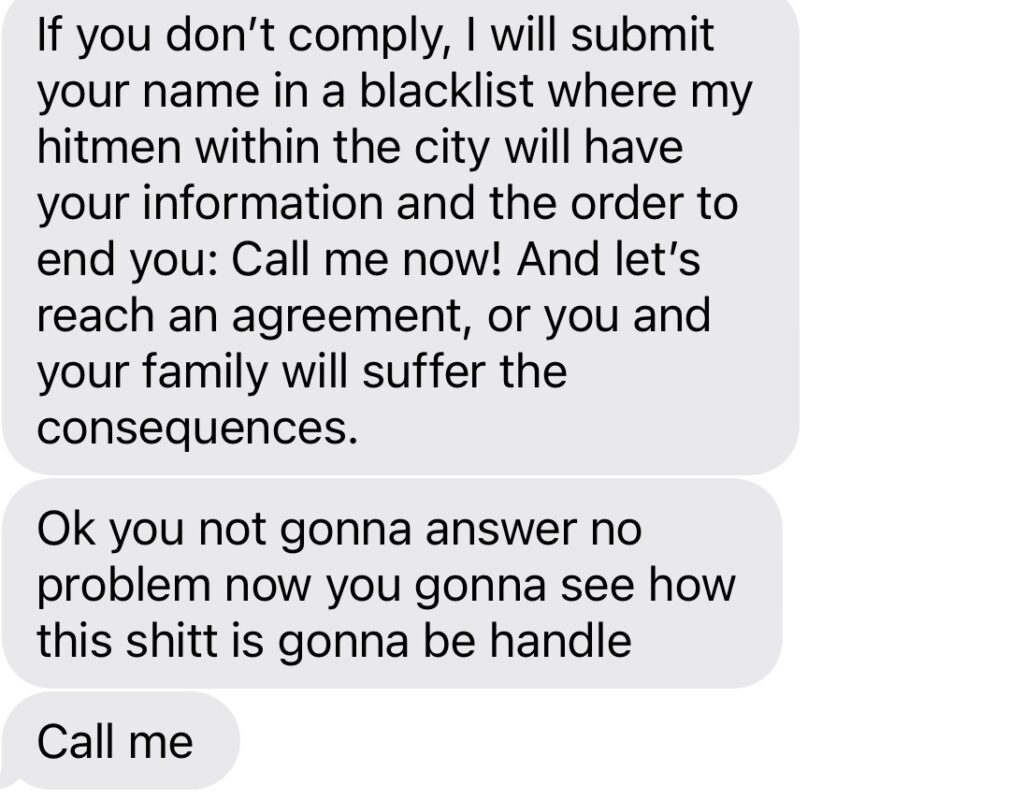
There were also some disturbing images with that text.
In all, Tony used three different phone numbers, but none produced any results, indicating that they are “burner” phone numbers, most likely disconnected now.
Key Takeaways
Here is the point: Imagine that “Tony” is good and can find information on you, your family, etc. (It is on the Internet, after all. One can find anything, as long as one looks in the right places). Then, send those texts and images to your wife, girlfriend, boyfriend, husband, kids, and friends, along with that phone call that mentions you stealing from one of Tony’s escorts. That will ruin some relationships!
However, you must understand that this is a scam! Cartels are not coming after you; it’s a social engineering tactic based on fear. On the other hand, TTPs (Tactics, Techniques, and Procedures) are constantly changing, and they get aggressive (I am talking about a phone call). So, do yourself a favor and avoid situations like that at all costs; it is just not worth it.
It is highly advisable to use a good VPN (something like NordVPN). It will protect your identity on the Internet, even if websites claim anonymity. Never trust anyone on the Internet!

